Evaluating Software Defined Perimeter Solution for Multi-cloud and Hybrid IT Access – Analyst Perspective Part 1
*This post originally appeared on the Pulse Secure blog prior to the acquisition in December 2020, when Pulse Secure became part of Ivanti.
The Secure Access market is quickly evolving to take advantage of multi-cloud and hybrid IT resources. With the sudden surge of work-from-home and need for increased secure remote access capabilities, organizations are now re-thinking how to fortify defenses with a user- and application-centric approach while progressing workplace flexibility and productivity.
Recently, Jon Oltsik, Sr. Principal Analyst from ESG (Enterprise Strategy Group) sat down with Pulse Secure to answer key questions on Zero Trust, VPNs and evaluating Software Defined Perimeter solutions.
What are the key secure access challenges for hybrid IT?
Hybrid IT means mobile workers and devices need access to applications and services located in corporate data centers, public cloud services, and SaaS application providers. Organizations often try to provide this access using existing technologies like firewalls and VPNs, but this requires cumbersome policies enforced by multiple technologies. At best this is complex and adds a lot of operational overhead. At worst, it doesn’t work. At ESG, we’ve seen many hybrid IT network access projects like this fail, resulting in weeks or month of wasted time.
What zero trust advancements are available in VPN and what merits does SDP architecture bring?
VPN technology provides a good basis for SDP by providing things like strong authentication, device posture checking, and single sign-on. The key here is to build upon these VPN capabilities with SDP functionality like end-to-end network segmentation from a device to a specific application or service regardless of location. This reduces the attack surface while providing trusted network connections. Given the requirements of hybrid IT, organizations need it all – strong VPN and SDP functionality.
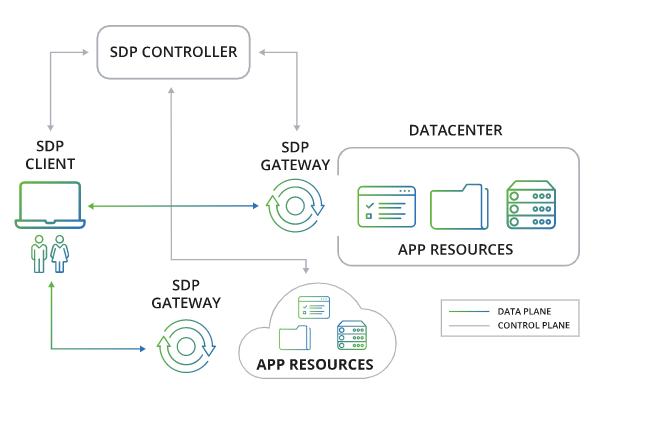
Organizations should seek out SDP technology that:
- Supports business needs and enforces security policies while remaining transparent to users
- Is easy to use, deploy, configure, and operate
- Verifies and authenticates users, devices, and security state
- Provides end-to-end trusted connections from devices to applications and services, regardless of location
- Provides broad application support
- Offers granular policies, automate gateway provisioning
- Provides continuous monitoring to enforce access and regulatory compliance