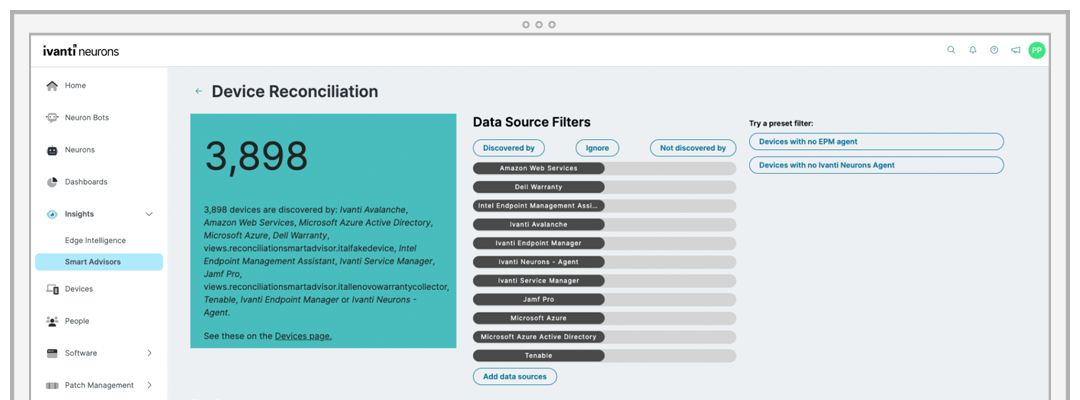
Ivanti Neurons for Discovery delivers accurate and actionable asset information in minutes. Determine what users and endpoints connect to the network, when they connect and what software is installed on them.
Accurate data
Discover and inventory all IT assets in real time to improve security posture.