Mandate Mania
Pursue Compliance with Confidence
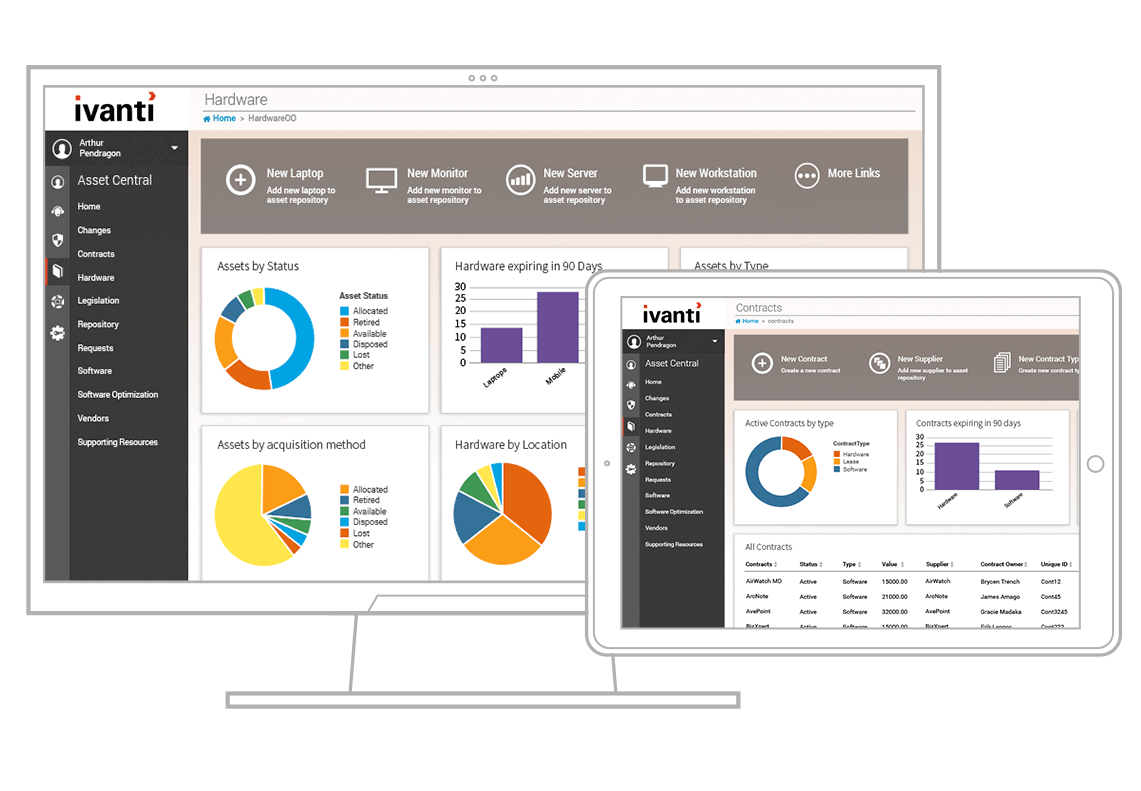
Mandates are put in place for good reason. Protecting tracked personally identifiable information (PII), meeting configuration baselines, and preventing cybersecurity threats are all unquestionably important. But compliance adds pressure on both budget and staff resources.
Ivanti helps your agency meet these mandates, whether originating from the Office of Management and Budget (OMB) in the USA, your federal government’s equivalent office, state/provincial, or local government entities.