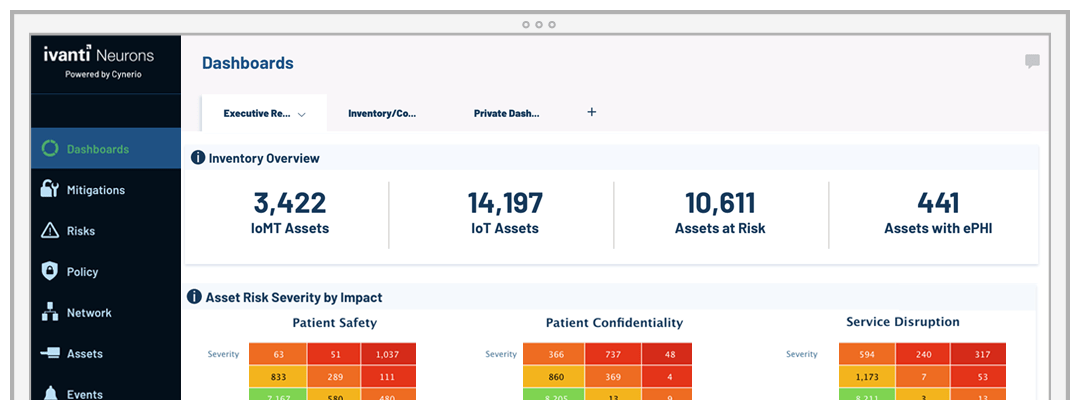
Increase productivity and keep employees happy by letting Ivanti's healthcare-focused technology manage and secure your endpoints from end to end, ensuring patient safety, data confidentiality and service availability. Discover and remediate all your hardware and software assets and easily run reports.
Secure patient records
Confidentiality of Electronic Health Records (EHRs) is critical, as is access for those delivering care.