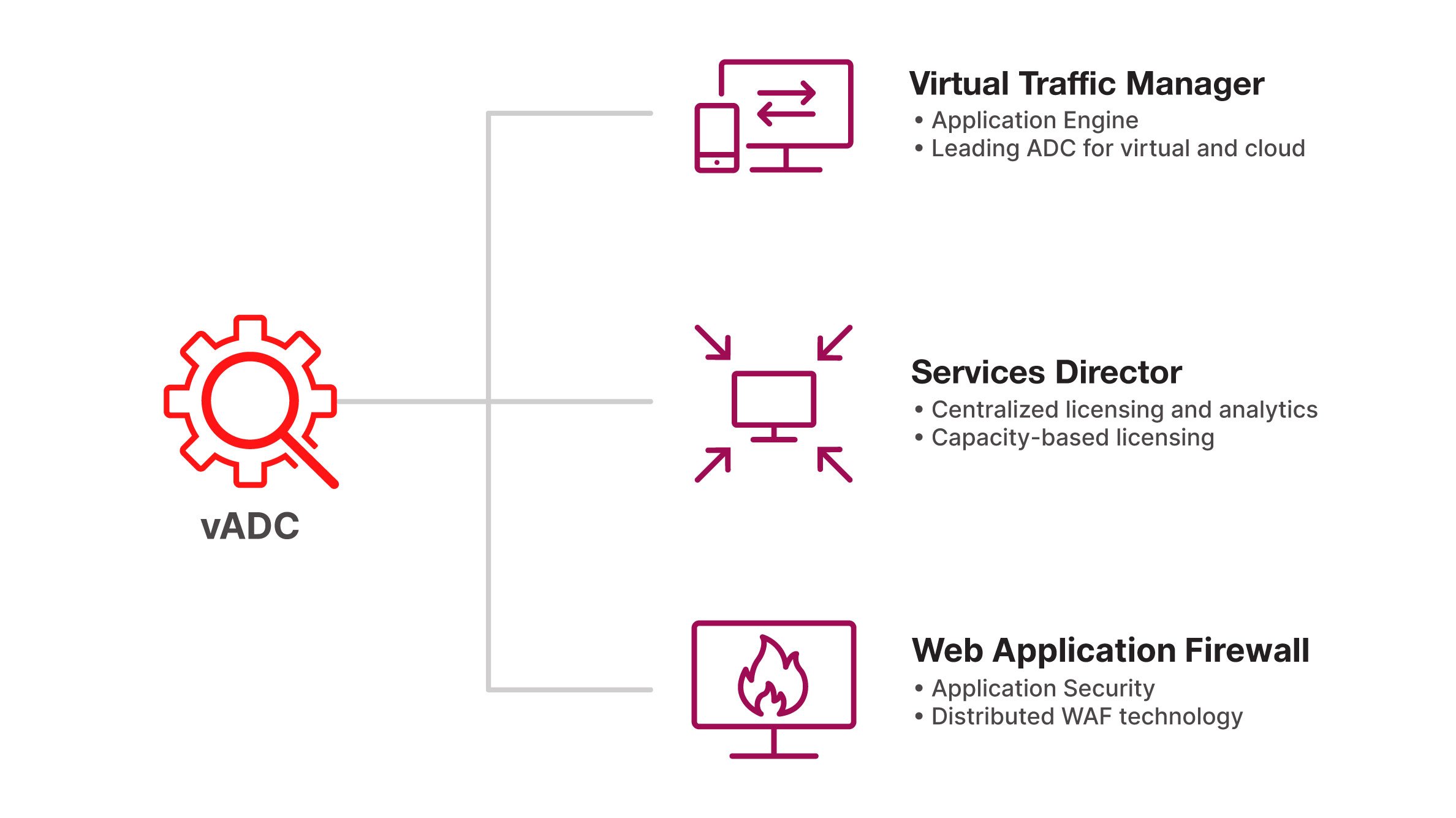
Mix and match Virtual Traffic Manager, Services Director and Web Application Firewall.

Ivanti vADC
Application Delivery Controller Solution
Deliver reliable applications with predictable performance and strong multi-layered security. Ivanti Virtual Application Delivery Controller (vADC) drives more transactions, even at peak load conditions, ensuring continuous uptime and real-time security monitoring of application traffic.
Virtual Traffic Manager
Unprecedented scale and flexibility to elevate performance and security for wide-ranging applications.

Services Director
Right-size and automate virtual ADCs to drive significant cost savings with true capacity-based licensing.

Web Application Firewall
Secure applications, help meet PCI-DSS compliance requirements and protect application layer attacks.

Ivanti Virtual Application Delivery Controller
The Ivanti Virtual Application Delivery Controller Solution is composed of three products which can be combined to suit the needs of any application.
Get Started
Ready to deliver secure, agile and responsive applications? Get started today.